Hash Values Are Used for Which of the Following Purposes
In the Oracle database hash functions are used for hash joins hash partitioning and hash clusters to name just a few examples. The following assumption can be taken.
Hash Functions Definition Usage And Examples Ionos
Plain text can easily be read by hackers that can be used by them for malicious purposes.
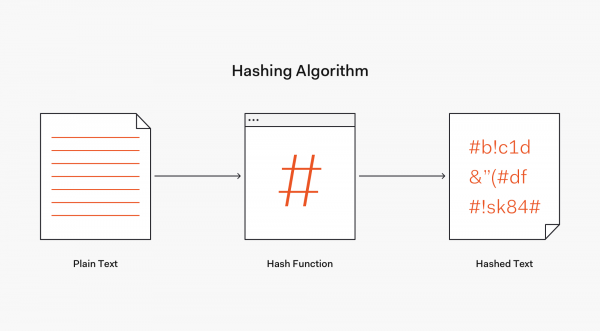
. In either case you need to compare two computed hashes. Hashing is the transformation of a string of character s into a usually shorter fixed-length value or key that represents the original string. Any two values of type FLOAT that can be converted to NUMBER38 0 without loss of precision will hash to the same value.
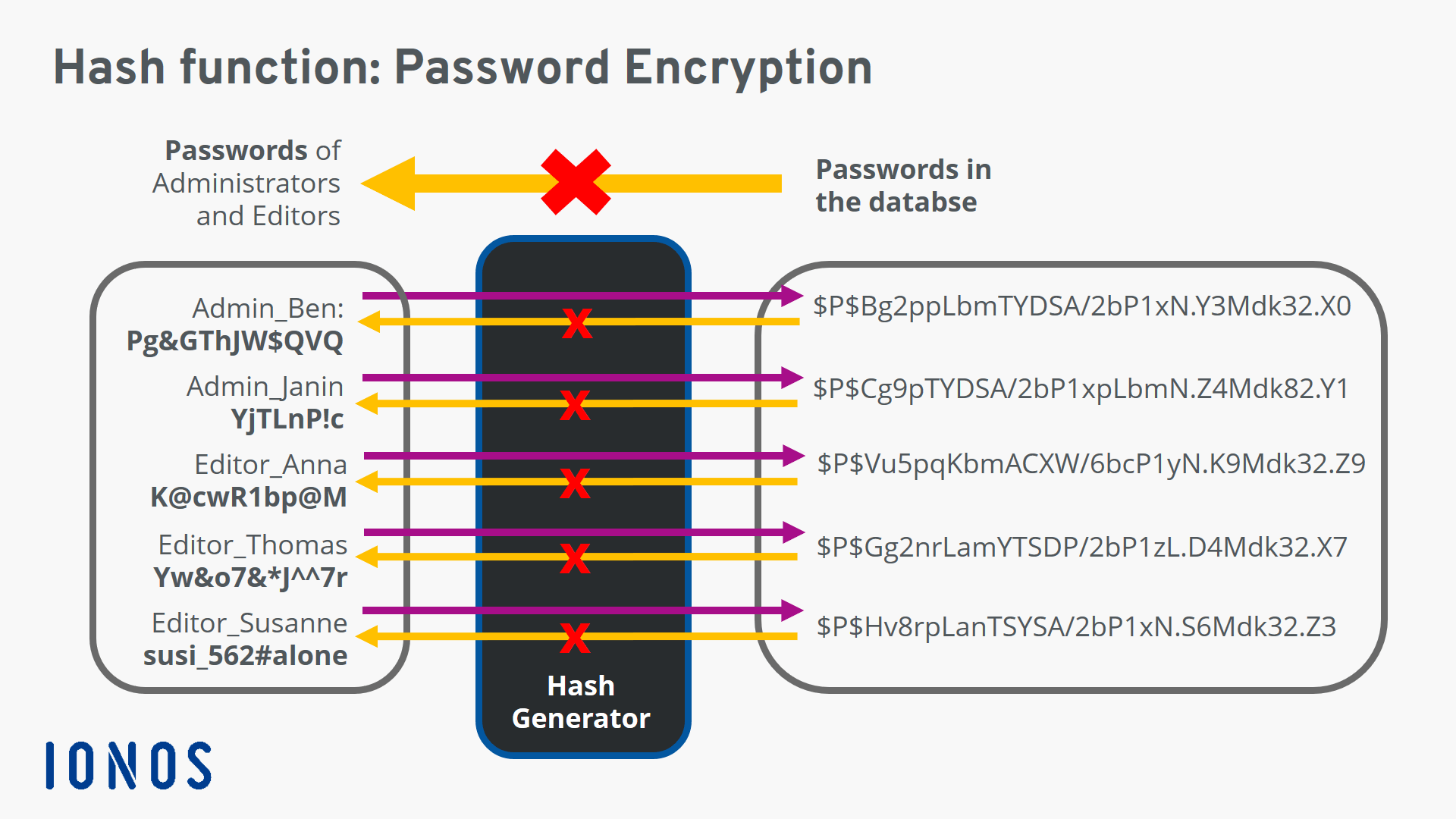
SELECT FROM employees WHERE employee_id v_empid. The password hash value which is a one-way mathematical representation of a password can be used directly as an authenticator to access services on behalf of the user through single sign-on SSO authentication. To illustrate the principle of a hash function I use the expression MODn 7 as a hash function in the following example.
Assumption J uniform hashing assumption. Keys are converted to arrays indices by hash function. It is also used in many encryption.
1 Message Digest MD5. Compare two hash values. Do not use the hash code as the key to retrieve an object from a keyed collection.
Ideally the only way to find a message that produces a given. This result will be the value of the whole method call expression. Its easy if theyre both stored as hexadecimal strings as in the last step of the above.
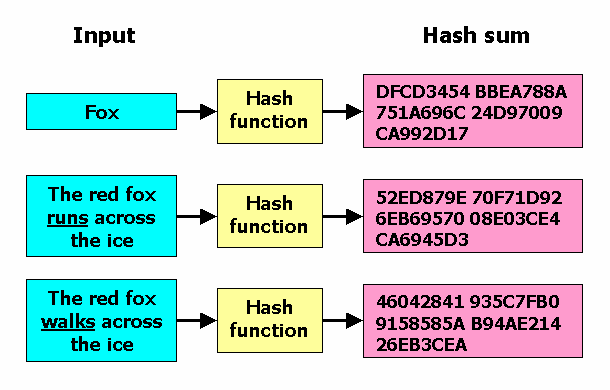
Hashing is used to index and retrieve items in a database because it is faster to find the item using the shorter hashed key than to find it using the original value. The following table shows the precedence. For the same input value the result is always the same.
The function is deterministic ie. The MD5 checksum for the following phrase is a long string of characters that represent that sentence. It is important that for a good hash function two different values for a and b should be considered hasha hashb.
You then use your own checksum calculator to produce a checksum using the same cryptographic hash function MD5 in this. To a password theft attack but it relies on stealing and reusing password hash values rather than the actual plaintext password. The following example shows a query that uses v_empid as a bind variable.
For our purposes here they essentially equal each other. But for several hash functions on a normal group of supercomputers millions of years has to be needed to find such values. Hashing is useful for rapid lookups of data in a hash table.
The following are the most used hashing functions. Ciphertext is a scrambled text that cannot be understood by the invaders if they somehow. It transforms an n element user-specified keyword set W into a perfect hash function FF uniquely maps keywords in W onto the range 0k where k n-1If k n-1 then F is a minimal perfect hash functiongperf generates a 0k element static lookup table and a pair of C functions.
For example the following all return the same hash value. Gperf is a perfect hash function generator written in C. You can create different hash values for different data.
Hashing with separate chaining. A hash code is not a permanent value. The advantage there of MD5 for example is speed of computation that fact that they are insecure is then irrelevant.
Do not serialize hash code values or store them in databases. A hash code is intended for efficient insertion and lookup in collections that are based on a hash table. Functions with these properties are used as hash functions for a variety of purposes not only in cryptographyPractical applications include message integrity checks digital signatures authentication and various information security applications.
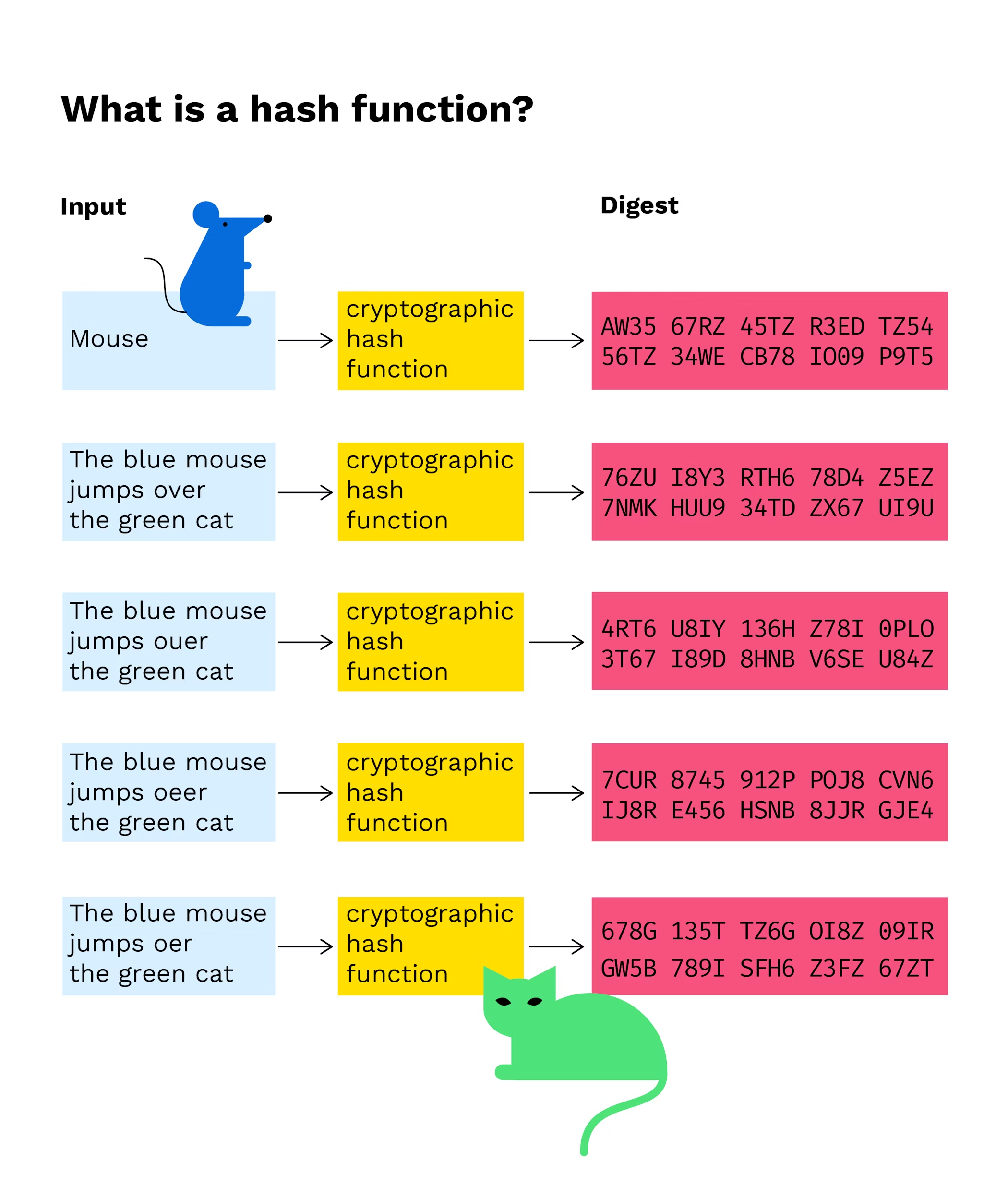
A cryptographic hash function CHF is a mathematical algorithm that maps data of an arbitrary size often called the message to a bit array of a fixed size the hash value hash or message digestIt is a one-way function that is a function for which it is practically infeasible to invert or reverse the computation. However making even a slight change like removing j. The purposes of creating a hash from source data are.
FYI It IS perfectly legitimate to use MD5 or SHA1 if your not using the hash as a cryptographic hash for example as a hash of content for comparison. We will have to assume that the hash function which we are using is uniformly distributing the keys amongst the integer values ranging between 0 to M-1. Any two values of type NUMBER that compare equally will hash to the same hash value even if the respective types have different precision andor scale.
Algorithms such as brute force are available to identify such values for good hash functions. Providing a way to see if data has changed over time. Note that hash concatenation is not to be used for many repeated concatenations like for adding items to a hash inside a loop.
A database index in which the database stores a bitmap for each index key instead of a list of rowids. Comparing two values without ever working with the actual values. You can compare hashes too.
A hash function takes a string of any length as input and produces a fixed length string which acts as a kind of signature for. The method call operation passes these values to the method which will in turn return a result.
Md5 Vs Sha 1 Vs Sha 2 Which Is The Most Secure Encryption Hash And How
What Is A Hash Function In A Blockchain Transaction Bitpanda Academy
Belum ada Komentar untuk "Hash Values Are Used for Which of the Following Purposes"
Posting Komentar